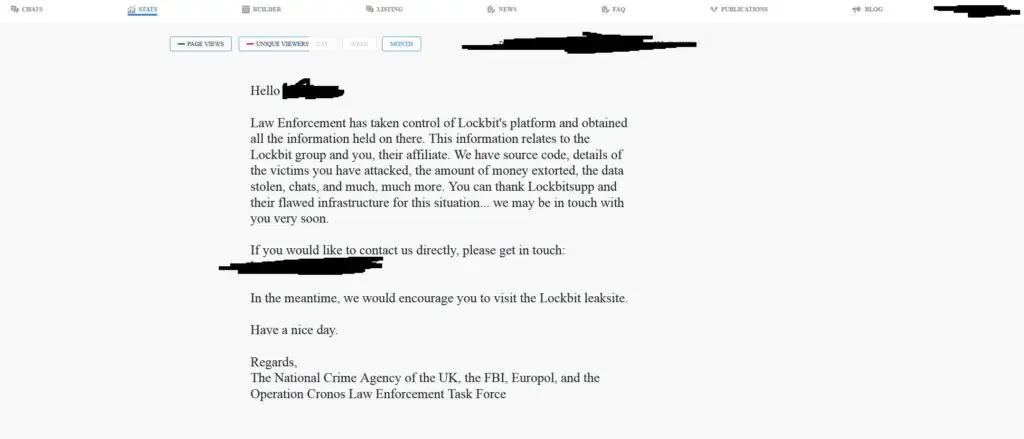
You may have heard of “technical debt”, but have you heard of “security debt”? In this episode, Jay and Joao will tell you all about it and why it’s a major issue for organizations.
Thanks to TuxCare for sponsoring the Enterprise Linux Security podcast. Check out their awesome services to see how they can simplify Linux administration!