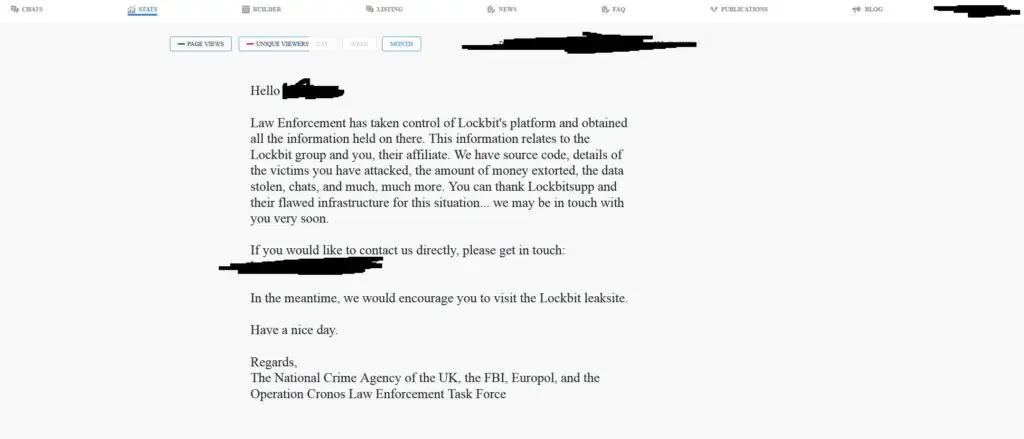
In this episode, Jay and Joao talk about a story that’s every cloud administrator’s worst nightmare – your entire environment, backups, everything – gone. That’s exactly what happened to UniSuper, a customer of Google Cloud. In this cautionary tale, we’ll explore the case of the missing cloud.
Thanks to TuxCare for sponsoring the Enterprise Linux Security podcast. Check out their awesome services to see how they can simplify Linux administration!
Note: The video version of this episode was edited and re-uploaded, in order to fix audio issues.