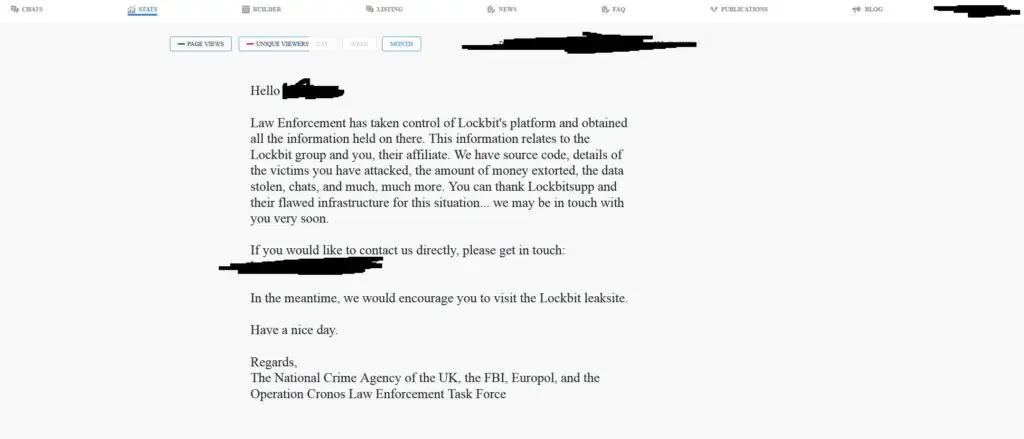
On this podcast, Jay and Joao have discussed multiple times a situation where a threat actor submits a pull request that’s more than the project bargained for. And now, we have a situation where OpenSSH was (almost) backdoored by a commit by a maintainer of the xz project. Don’t miss this episode for all the details!
Thanks to TuxCare for sponsoring the Enterprise Linux Security podcast. Check out their awesome services to see how they can simplify Linux administration!