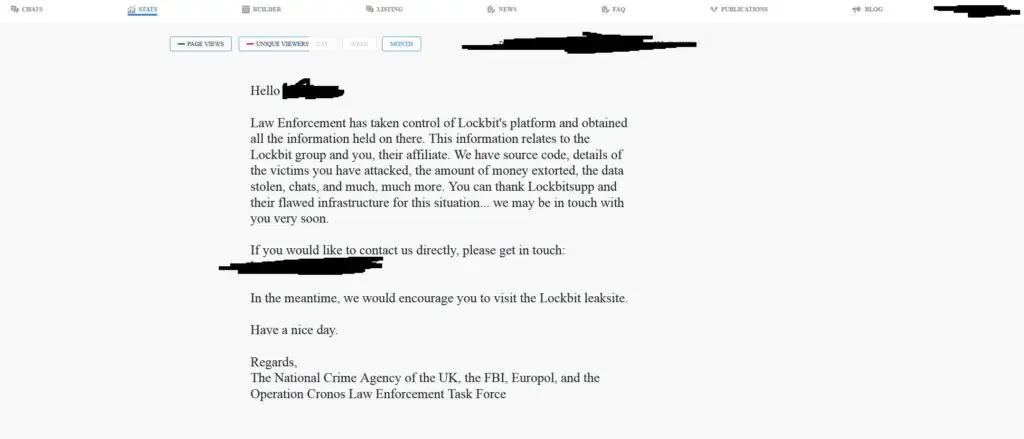
In the last episode, we discussed a story where a company literally lost their cloud – at no fault of their own. But what is truly your responsibility when working with a cloud provider? What is their responsibility? In this episode, Jay and Joao discuss where the line is drawn between you and your cloud provider.
Thanks to TuxCare for sponsoring the Enterprise Linux Security podcast. Check out their awesome services to see how they can simplify Linux administration!